Expert Guidance on Traffic Tickets in NYCTable of Contents Navigating New York City's Traffic Laws Understanding the Penalties of Traffic Violations Choosing the Right Traffic Lawyer in NYC Deciphering the Legal Process in Traffic Cases Client Experiences with Traffic Attorneys NYCManaging New York City's Traffic Violations Ha
Rumored Buzz on seo agency baltimore
Enhancing Your Digital Footprint with a Top Local SEO Expert in BaltimoreTable of Contents Why Your Business Needs SEO in Baltimore Selecting the Right Local SEO Expert in Baltimore Understanding the Services Offered by Local SEO Experts in Baltimore Optimizing Google My Business for Enhanced Local Visibility Satisfied Clients Sh
Rumored Buzz on attorney seo baltimore
Enhancing Your Digital Footprint with a Top Local SEO Expert in BaltimoreTable of Contents The Importance of SEO in Baltimore Selecting the Right Local SEO Expert in Baltimore Discovering the Services Offered by SEO Agencies in Baltimore Mastering Google My Business for Superior Local Visibility Satisfied Clients Share Their Expe
Ernie's Carpet Cleaning Grove OK Options
Discover Top-notch Carpet Cleaning Services in the Grand Lake AreaTable of Contents What Sets Our Cleaning Apart Explore Our Cleaning Solutions Benefits of Professional Carpet Cleaning Serving Your Community Hear From Our Satisfied ClientsWhy Our Carpet Cleaning Services Are the Best Choice When looking for carpet cleaning nea
The Basic Principles Of Atlanta ENT DR
Discovering Excellence in Atlanta ENT DoctorsTable of Contents Why Choose Expert ENT Care in Atlanta Comprehensive ENT Services Offered in Atlanta How to Choose the Best ENT Specialists in Atlanta The Impact of Advanced ENT Technologies in Atlanta Success Stories: Why They Love Our ENT CareDiscovering the Best Atlanta ENT Doctors
 Emilio Estevez Then & Now!
Emilio Estevez Then & Now! Rider Strong Then & Now!
Rider Strong Then & Now! Lark Voorhies Then & Now!
Lark Voorhies Then & Now!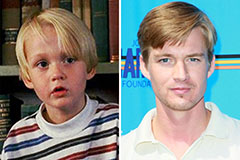 Mason Gamble Then & Now!
Mason Gamble Then & Now! Andrea Barber Then & Now!
Andrea Barber Then & Now!